Research on the Safety Evaluation Method of Seismic Information System Based on AHP
-
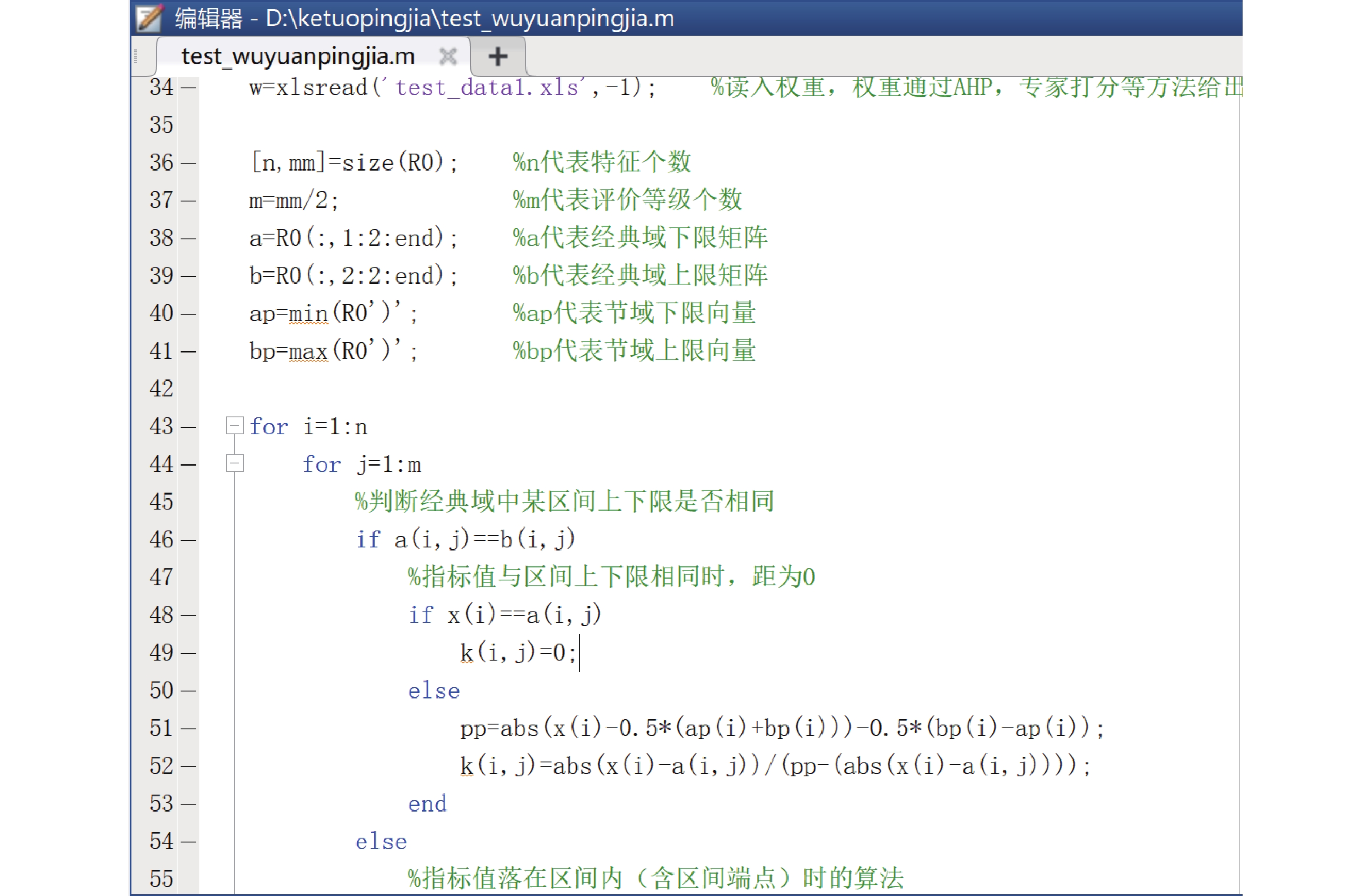
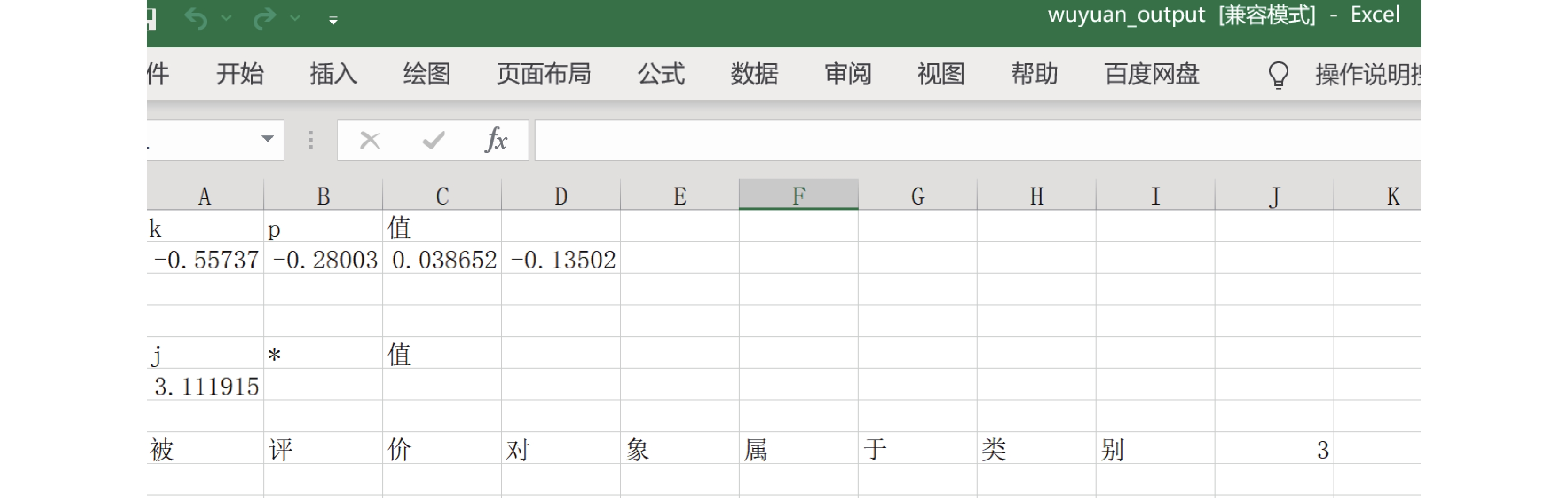
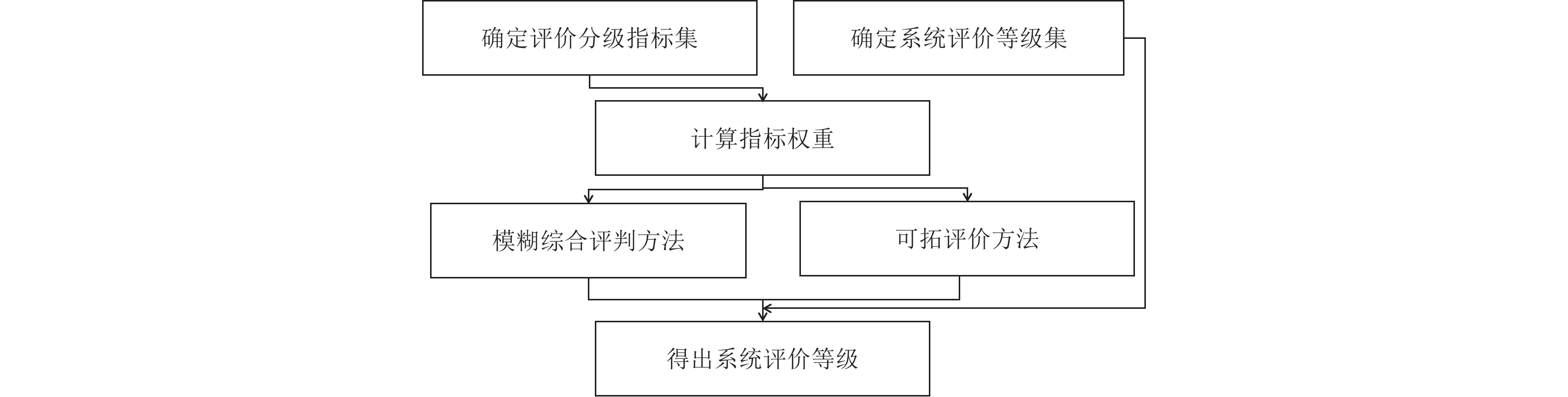
摘要: 为有效应对网络安全问题,加强地震信息系统网络安全,网络工程师做了大量工作,如增加网络防护、开展安全演练等,但在网络安全评价体系和评价方法方面开展的研究相对较少。本文结合《信息安全技术 网络安全等级保护测评要求》(GB/T 28448—2019)要求,基于AHP(层次分析法)获取系统评价权重指标,分别利用模糊综合评判方法和可拓方法对地震信息系统实例进行安全等级评价,并对比2种评判方法,验证其在地震信息系统安全评价工作中的应用效果。本研究采用量化的客观评价方法,可为信息系统安全评价、风险识别、安全等级保护等提供参考。Abstract: In order to effectively address network security problems and strengthen the network security of seismic information systems, information network engineers have done a lot of works, such as strengthening network protection and conducting security drills, but relatively few researches have been conducted on network security evaluation systems and evaluation methods. In this paper, we combine the requirements of “Information Security Technology —Evaluation Requirement for Classified Protection of Cybersecurity (GB/T 28448—2019)” , obtain system evaluation weight indicators based on AHP (hierarchical analysis method), and then evaluate the security level of seismic information system instances using the fuzzy comprehensive evaluation method and the topizable method, respectively, and compare and analyze the two evaluation methods to verify the effectiveness of the application of the two methods in the seismic information system security evaluation work. This study adopts a quantitative and objective evaluation method, which can provide reference for information system security evaluation, risk identification, and security level protection.
-
表 1 4种标度法赋值说明
Table 1. Description of the 4 kinds of scaling methods assignment
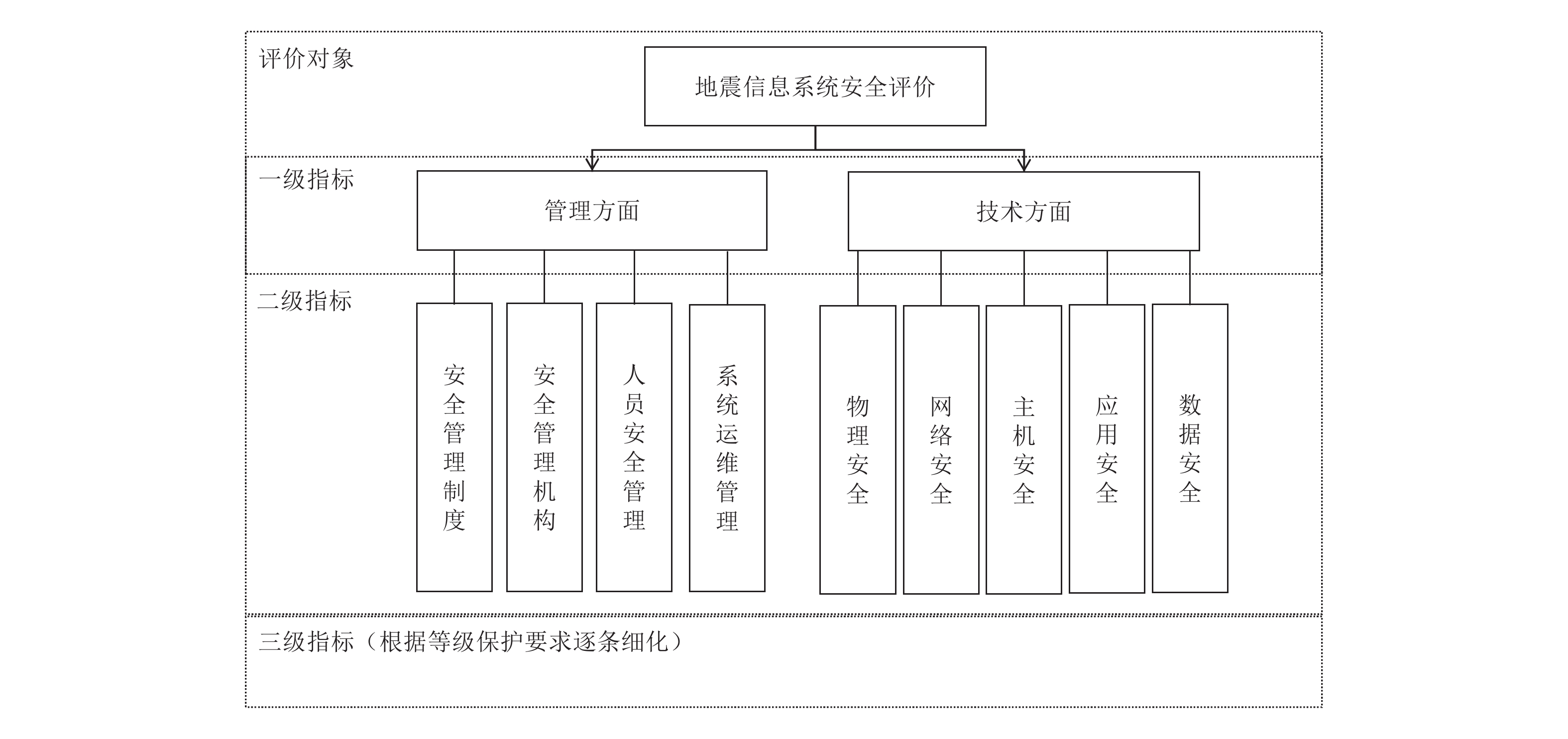
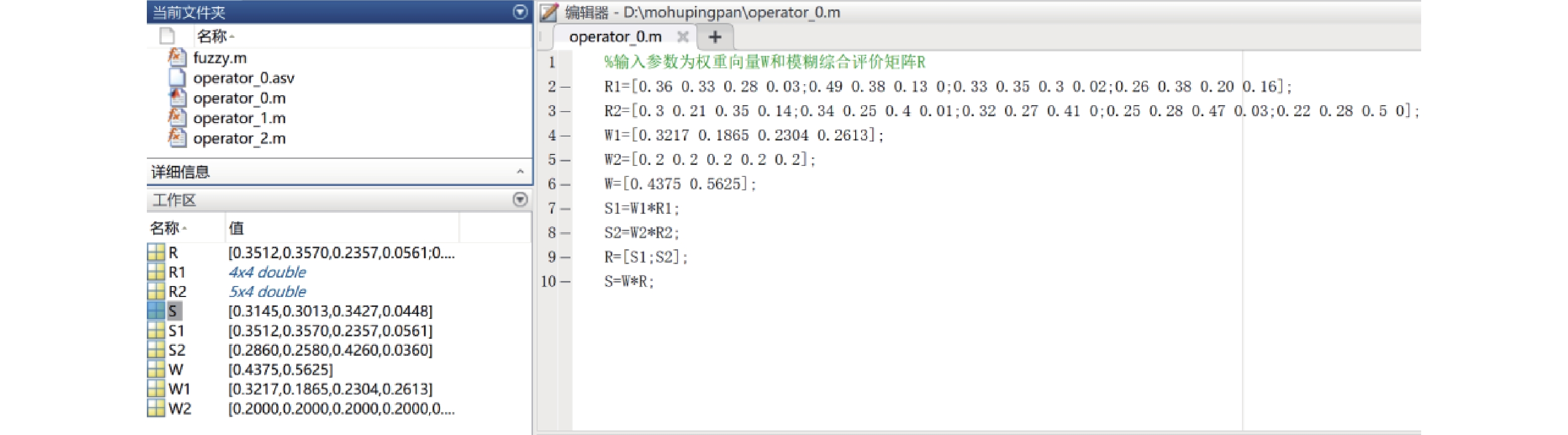
等级划分 1~9标度法 9/9~9/1标度法 10/10~18/2标度法 指数标度法 相同 1 9/9 10/10 90 稍微大 3 9/7 12/8 9(1/9) 明显大 5 9/5 14/6 9(3/9) 强烈大 7 9/3 16/4 9(6/9) 极端大 9 9/1 18/2 9(9/9) 表 2 2层指标权重、打分及隶属度投票示例
Table 2. The weights and scoring example of the second level indexes
安全指标 权重 打分 优 良 合格 不合格 安全管理制度 0.1407 90 36 33 28 3 安全管理机构 0.0816 90 49 38 13 0 人员安全管理 0.1008 95 33 35 30 2 系统运维管理 0.1143 90 26 38 20 16 物理安全 0.1125 85 30 21 35 14 网络安全 0.1125 85 34 25 40 1 主机安全 0.1125 80 32 27 41 0 应用安全 0.1125 90 25 28 47 3 数据安全 0.1125 92 22 28 50 0 -
蔡文, 1995. 从物元分析到可拓学. 北京: 科学技术文献出版社. 陈欣, 卢海宏, 薄万举, 2020. 可拓方法在地震信息系统安全评价中的应用研究. 地震工程学报, 42(5): 1337—1342 doi: 10.3969/j.issn.1000-0844.2020.05.1337Chen X. , Lu H. H. , Bo W. J. , 2020. Application of the extension method to the safety evaluation of seismic information systems. China Earthquake Engineering Journal, 42(5): 1337—1342. (in Chinese) doi: 10.3969/j.issn.1000-0844.2020.05.1337 傅钰, 2018. 网络安全等级保护2.0下的安全体系建设. 网络安全技术与应用, (8): 13, 16. 孔睿, 何韶军, 焦大伟等, 2020. 基于服务重要度的信息系统安全评估方法. 网络安全技术与应用, (6): 30—33. 李洪兴, 汪培庄, 1994. 模糊数学. 北京: 国防工业出版社. 李青, 2015. 基于AHP和模糊综合评判法的大学等级排行评价研究. 价值工程, 34(34): 17—19Li Q. , 2015. Study of the evaluation of university level ranking based on AHP and fuzzy comprehensive evaluation method. Value Engineering, 34(34): 17—19. (in Chinese) 李钊, 徐国爱, 班晓芳等, 2013. 基于元胞自动机的复杂信息系统安全风险传播研究. 物理学报, 62(20): 200203 doi: 10.7498/aps.62.200203Li Z. , Xu G. A. , Ban X. F. , et al. , 2013. Complex information system security risk propagation research based on cellular automata. Acta Physica Sinica, 62(20): 200203. (in Chinese) doi: 10.7498/aps.62.200203 刘智慧, 2004. 可拓方法在信息安全评价中的应用. 电力信息化, 2(9): 41—42. 鲁县华, 2011. 民航空管系统安全评估技术研究. 天津: 天津大学.Lu X. H., 2011. Safety assessment technique research of civil aviation ATC system. Tianjin: Tianjin University. (in Chinese) 国家市场监督管理总局, 中国国家标准化管理委员会, 2019. GB/T 28448—2019 信息安全技术 网络安全等级保护测评要求. 北京: 中国标准出版社.State Administration for Market Regulation, Standardization Administration of the People's Republic of China, 2019. GB/T 28448—2019 Information security technology-evaluation requirement for classified protection of cybersecurity. Beijing: Standards Press of China. (in Chinese) 王帆, 霍明奎, 王晓婷, 2014. 基于模糊灰度的信息系统安全风险评价与对策. 情报科学, 32(1): 110—114Wang F. , Huo M. K. , Wang X. T. , 2014. Information system security risk assessment based on the fuzzy gray-level and countermeasures. Information Science, 32(1): 110—114. (in Chinese) 王丰, 张春平, 林瑜等, 2018. 军事院校信息系统安全风险的可拓识别评估. 武汉理工大学学报(信息与管理工程版), 40(6): 606—609 doi: 10.3963/j.issn.2095-3852.2018.06.003Wang F. , Zhang C. P. , Lin Y. , et al. , 2018. Extension identification assessment of information system security risk in military academies. Journal of Wuhan University of Technology (Information & Management Engineering), 40(6): 606—609. (in Chinese) doi: 10.3963/j.issn.2095-3852.2018.06.003 王海燕, 2016. 基于GRA-RBF神经网络的信息安全风险评价. 内蒙古师范大学学报(自然科学汉文版), 45(2): 166—169, 173 doi: 10.3969/j.issn.1001-8735.2016.02.004Wang H. Y. , 2016. Information security risk assessment model based on GRA-RBF neural network. Journal of Inner Mongolia Normal University (Natural Science Edition), 45(2): 166—169, 173. (in Chinese) doi: 10.3969/j.issn.1001-8735.2016.02.004 吴晨, 董吉文, 房晓亮等, 2013. 地震行业信息安全体系建设. 地震地磁观测与研究, 34(3—4): 245—251Wu C. , Dong J. W. , Fang X. L. , et al. , 2013. Earthquake profession information security system construction research. Seismological and Geomagnetic Observation and Research, 34(3—4): 245—251. (in Chinese) 谢季坚, 刘承平, 2000. 模糊数学方法及其应用. 2版. 武汉: 华中理工大学出版社.Xie J. J., Liu C. P., 2000. Fuzzy mathematical methods and their applications. 2nd ed. Wuhan: Huazhong University of Science & Technology Press. (in Chinese) 薛晓锋, 2010. 斜拉桥拉索阻尼器的选型评价. 西安: 长安大学, 81—90Xue X. F. , 2010. Evaluation for selecting cable dampers of cable-stayed bridge. Xi’an: Chang'an University, 81—90. (in Chinese) 杨春燕, 蔡文, 2014. 可拓学. 北京: 科学出版社, 70—170Yang C. Y. , Cai W. , 2014. Extenics. Beijing: Science Press, 70—170. (in Chinese) 张益, 2012. 信息安全等级保护模糊综合评价模型研究. 见: 第二届全国信息安全等级保护测评体系建设会议论文集. 上海: 《信息网络安全》北京编辑部, 129—133. 周利霞, 王晓磊, 杨奕等, 2013. 天津地震信息网络系统的安全建设. 震灾防御技术, 8(3): 334—339 doi: 10.3969/j.issn.1673-5722.2013.03.013Zhou L. X. , Wang X. L. , Yang Y. , et al. , 2013. Safety construction of Tianjin seismic information network system. Technology for Earthquake Disaster Prevention, 8(3): 334—339. (in Chinese) doi: 10.3969/j.issn.1673-5722.2013.03.013 Cai W. , Yang C. Y. , Zhao Y. , et al. , 2004. New development of the basic theory of extenics. Engineering Sciences, 2(1): 40—45. -


 下载:
下载: